We agree
upon conditions for successful cooperation: select the deployment facility, define the objective, select the Kaspersky MLAD deployment option, set up a working group, and sign the relevant agreements.
We study
the deployment facility: collect technological data to build an ML model, and jointly develop a Kaspersky MLAD connection project.
We build
an ML model and compile a list of anomalies that it detects in the technological data provided. We set up the equipment.
We deploy
Kaspersky MLAD at the facility and connect it to the data flow.
We put
Kaspersky MLAD into operation. We train the customer’s employees to work with Kaspersky MLAD. We analyze anomalies detected during operation, and fine-tune the ML model.
We maintain
Kaspersky MLAD. We provide standard technical support. As a separate service, we offer to build a new ML model if the technological process changes.
Stage 1. We agree upon the conditions for successful cooperation
We select the deployment facility, define the objective, decide on the Kaspersky MLAD deployment option, set up a working group, and sign the relevant agreements
Is the necessary data about the facility available?
Make sure you collect telemetry data at the facility where Kaspersky MLAD is to be integrated; you can download the telemetry history from the ICS database in any format (for example, CSV or HDF5). Historical data is required to create the ML model.
To operate correctly, Kaspersky MLAD needs telemetry data with the following characteristics:
Should contain multiple (from 10 to 10,000) parameters. For example, data from industrial systems can consist of sensor readings, setpoint values, or actuator commands.
Parameters should have numerical values or be reducible to them. For example: valve closed – 0, open – 1.
Parameter values should be time-related and vary with time; the time of telemetry sources should be synchronized. The frequency of data updates should range from 100 milliseconds to 24 hours.
The values of the various parameters should be interconnected (by physical laws, control logic, process logic, etc.).
The parameters should include those of the most observational significance, and those that lie at (or as close as possible to) the root cause of the anomaly which is affecting various other parameters.
Which Kaspersky MLAD deployment option is most suitable for you?
Kaspersky MLAD is usually deployed on-premises.
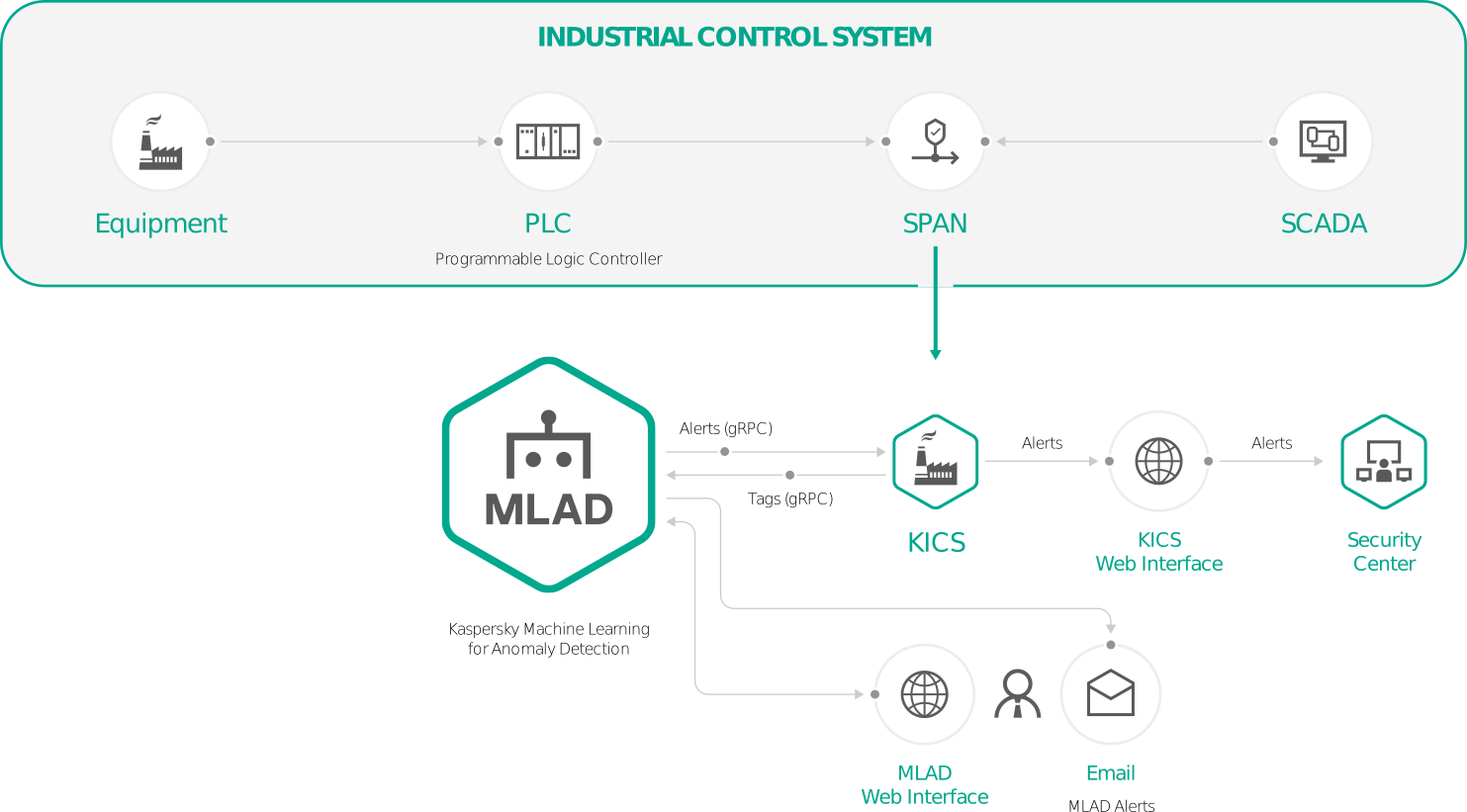
Combined with Kaspersky Industrial CyberSecurity for Networks
For this option, Kaspersky Industrial CyberSecurity for Networks must be installed at the deployment facility together with Kaspersky MLAD, and the two solutions must be connected. Kaspersky Industrial CyberSecurity for Networks analyzes mirrored traffic and sends tags to Kaspersky MLAD in online mode. Kaspersky MLAD returns information about detected anomalies. In this integration, Kaspersky MLAD receives tags using the gRPC protocol via the Kaspersky Industrial CyberSecurity for Networks connector.
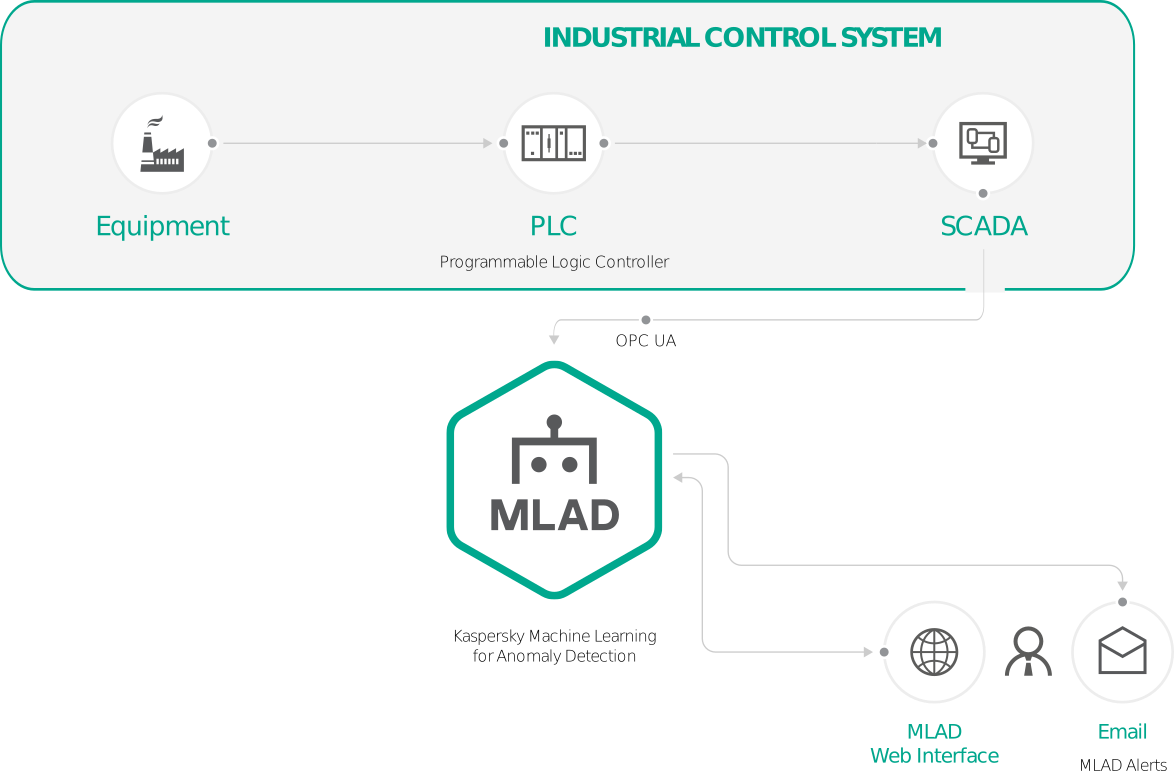
Kaspersky MLAD standalone installation
In this case, Kaspersky MLAD is installed as a standalone solution and uses an OPC UA connector to receive data using the protocol described in the OPC Unified Architecture specification. For this, the deployment facility must be able to transfer tags from the ICS via the OPC UA protocol in online mode.
If the standard deployment options do not suit your requirements, our Kaspersky MLAD integration experts can suggest other deployment options. Kaspersky MLAD receives and handles telemetry data from IoT devices. In addition, the bundled HTTP Connector component can be used to configure the scheduled upload of tags in the form of CSV files from the SCADA Historian database, using the HTTP protocol (for example, a script that uploads data every hour or every minute).
Who are the working group members?
To implement Kaspersky MLAD, a working group made up of Kaspersky MLAD integration experts and your IT specialists, IT security specialists, process engineers and operators needs to be set up. The group should consist of experts authorized to make decisions. For deployment with Kaspersky Industrial CyberSecurity for Networks, it is important the group contain experts with experience of integrating this solution.
Communication channels and security clearances
For successful implementation, clear communication channels must be established between working group members, and the conditions for admitting Kaspersky MLAD integration experts to the deployment facility must be agreed upon. The communication channels must support the transfer of large amounts of data (for example, gigabytes of historical data from the ICS). The integration experts will need physical access to the Kaspersky MLAD servers. Remote access to them via the SSH protocol will speed up implementation.
Agreements
The first stage also includes the signing of a non-disclosure agreement (NDA), a license agreement, and a service contract for building the ML model.
Stage 2. We study the deployment facility
We collect technological data to build the ML model. We develop a Kaspersky MLAD connection project.
We collect data to build the ML model
Kaspersky MLAD is based on an artificial neural network. This neural network needs to be trained on historical telemetry data obtained from the deployment facility, and its operating parameters need to be set – an ML model needs to be built. Before building the ML model, our Kaspersky MLAD integration experts have to determine the key tags in the telemetry data and prepare a training set. To do so, they will need to consult the process engineers at the deployment facility and receive the following information:
- Flow diagrams of the deployment facility
- A list of loaded tags with descriptions, mapped to the flow diagrams
- A list of key tags for the technological process
- Historical telemetry data (from 1–2 months to a year)
We develop and approve the Kaspersky MLAD connection project
Kaspersky MLAD constitutes a set of Docker containers deployed on a server (see the Technologies section for more details). User access to Kaspersky MLAD is via the web interface. At this stage, the server location is determined, the Kaspersky MLAD deployment option is selected, and the equipment and infrastructure of the deployment facility are prepared in accordance with the Kaspersky MLAD requirements.
Network environment requirements
The network must have an NTP server to provide accurate times. Kaspersky MLAD must have access to it.
If you would like to receive anomaly detection alerts via email, an SMTP server must be deployed in the network. Kaspersky MLAD must be able to communicate with it.
If you select the option of deploying Kaspersky MLAD together with Kaspersky Industrial CyberSecurity for Networks, then during the installation of Kaspersky MLAD you will need to specify the fully qualified domain name (FQDN) of the server on which Kaspersky Industrial CyberSecurity for Networks is installed. This server must be accessible from the computer on which the Kaspersky MLAD system is installed.
If you select the Kaspersky MLAD standalone option, the Kaspersky MLAD server must be able to receive tags from the ICS via the OPC UA protocol in online mode.
Minimum target platform requirements for installing the server side of Kaspersky MLAD
Minimum hardware requirements:
- Intel Xeon E3 v6 processor
- 32GB RAM
- 2 x 1TB free space on the hard drive
The processor must support the following extensions for the TensorFlow 1.12.0 library:
- Advanced Vector Extensions (avx)
- Advanced Vector Extensions 2 (avx2)
- Streaming SIMD Extensions 3 (sse3) instruction set
- Streaming SIMD Extensions 4.1 (sse4_1) instruction set
- Streaming SIMD Extensions 4.2 (sse4_2) instruction set
- CMPXCHG16B (cx16) instruction
- POPCNT (popcnt) instruction
- Fused multiply-add (FMA) instruction set
Supported operating system
Ubuntu 18.04 LTS
Before deployment of Kaspersky MLAD on the server, the following software must be installed:
- docker-18.09.4-ce or higher
- docker-compose 1.23.2 or higher
Operator computer requirements
To use the Kaspersky MLAD web interface, the operator’s computer must meet the following minimum requirements:
- Intel Core i5-4570 processor
- 8GB RAM
- Google Chrome 56 or higher
- The minimum monitor resolution for the correct display of the web interface is 1600×900.
If the above requirements for the operator’s computer are met, the Monitoring section correctly displays up to 10 graphs with predictions (for example, for a preset of 10 tags).
Stage 3. We build the ML model for anomaly detection
We build the ML model and compile a list of anomalies it detects in the technological data provided. We set up the equipment.
To build the ML model, our Kaspersky MLAD integration experts must prepare a training set of telemetry data, which involves filtering out noise, selecting the most significant tags for anomaly detection, generating scaling rules, and presenting the data in the form required for the neural network. At this point, deficiencies in the telemetry data provided for training the neural network are identified. Help may be needed from your experts to supply a more representative data sample.
In the process of building the ML model, your process engineers may also be required to jointly analyze anomalies detected by the ML model in the training data sample.
In addition to building the ML model, at this stage the equipment and infrastructure are prepared for the deployment of Kaspersky MLAD.
Stage 4. We deploy Kaspersky MLAD
We deploy the Kaspersky MLAD server at the facility and connect it to the data flow
The deployment takes place in accordance with the Kaspersky MLAD connection project. The information network, equipment, and infrastructure should be prepared in accordance with the Kaspersky MLAD connection project.
For successful deployment, our Kaspersky MLAD integration experts need physical access to the server hosting platform. Remote access to the Kaspersky MLAD server via the SSH protocol will speed up implementation.
At this stage, the participation of the customer’s IT and process engineers will be required to resolve potential issues with the infrastructure and the capture of telemetry data by Kaspersky MLAD.
Deployment of Kaspersky MLAD is followed by testing, after which the system is connected to the online telemetry flow.
Stage 5. We put Kaspersky MLAD into operation
We train the customer’s employees to work with Kaspersky MLAD. We analyze anomalies detected during operation, and fine-tune the ML model.
At this stage, we create a test program for the Kaspersky MLAD run-in period, train the process engineers and operators to work with the system, and, together with the process engineers, analyze detected anomalies and present the results. Using the results of the analysis, we fine-tune the ML model.
Stage 6. We maintain Kaspersky MLAD
We provide standard technical support. As a separate service, we offer to build a new ML model if the technological process changes
Maintenance and support of Kaspersky MLAD can be performed both on-site, with Kaspersky MLAD integration experts visiting the facility, and remotely via the SSH protocol. Our experts will need Kaspersky MLAD logs and selected telemetry datasets.
If the technological process is substantially restructured or the operating mode is changed at the deployment facility, it may be necessary to build a new ML model. This service is provided separately.