Operating principles
Kaspersky MLAD detects anomalies using innovative, patented machine-learning technology
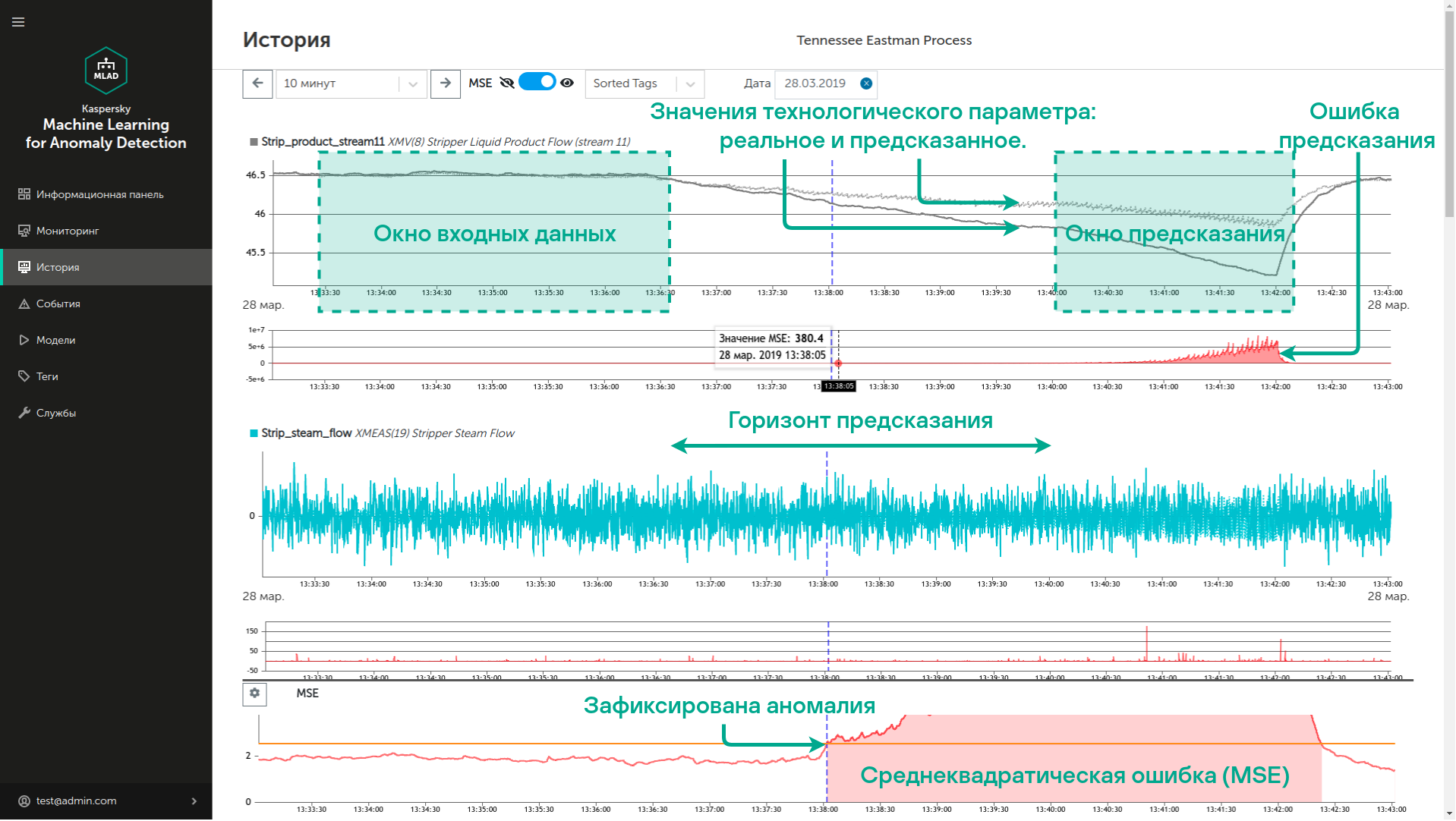
- Predictions are based on the aggregate technological parameter values already received over a certain period – the input window.
- On the basis of the input window, the neural network created using the ML model predicts what values the technological parameters should take during a certain time interval (prediction window) in the specified near future (prediction horizon).
- Using the difference between the predicted values of the technological parameters and those actually observed, Kaspersky MLAD calculates prediction errors for each parameter.
- Based on the aggregate prediction errors, Anomaly Detector calculates the mean square error (MSE). Each technological parameter is assigned a weight that is used in calculating the error. For example, for an ICS at a chemical plant, the readings of the pressure sensor inside the reactor are more important than the readings of the atmospheric pressure sensor on the plant floor, so a deviation in the former will have a greater impact on the overall error.
- An anomaly is recorded when the MSE exceeds a certain threshold, which is predefined in the ML model.
Advantages of the approach
- Identifies hard-to-detect anomalies caused by slight deviations in multiple parameters. This is made possible by observing aggregate process parameters.
- Logs anomalies in the early stages of development.
- Reduces the number of false alarms.
Input data
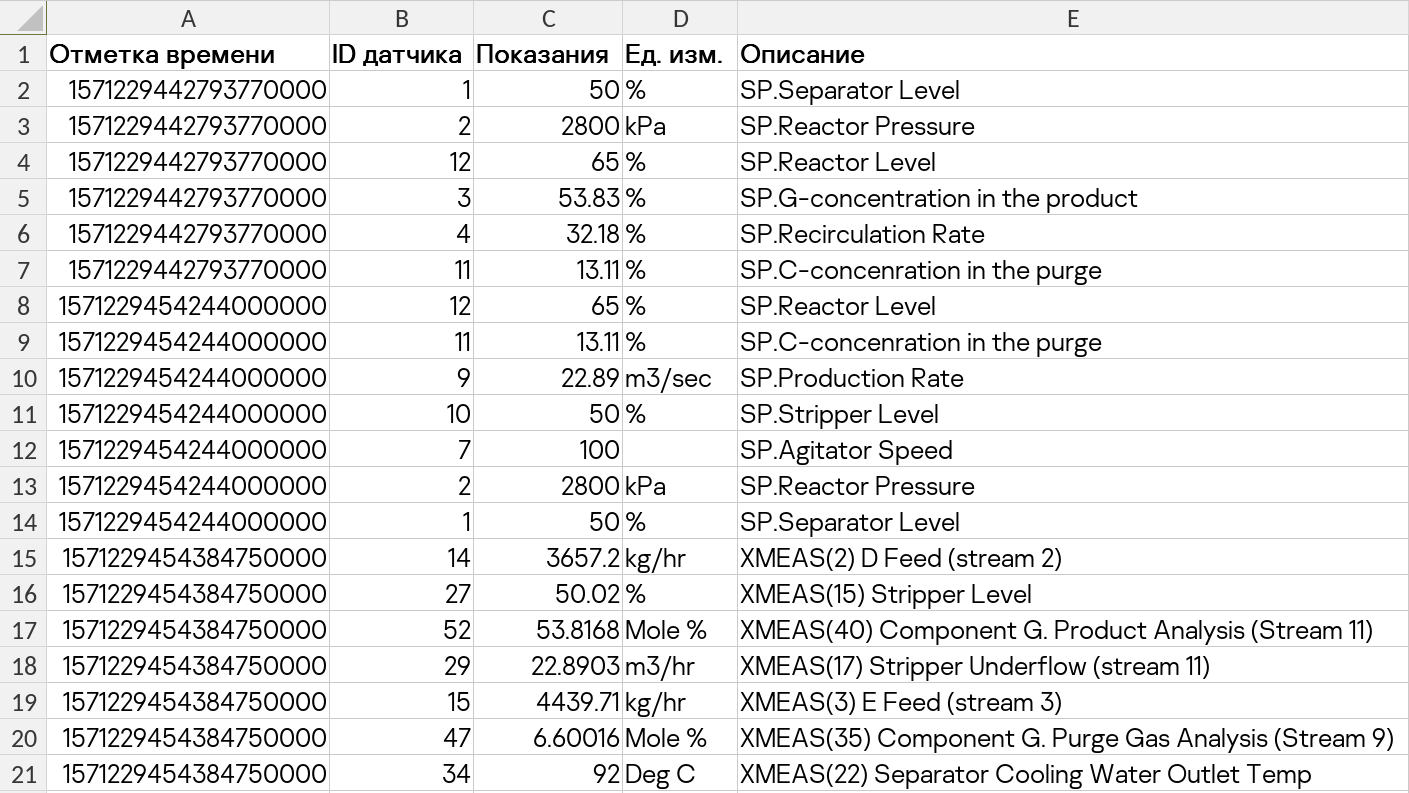
Kaspersky MLAD can operate with any telemetry data
- Should contain multiple (from 10 to 10,000) parameters. For example, data from industrial systems can consist of sensor readings, setpoint values, or actuator commands.
- Parameters should have numerical values or be reducible to them. For example: valve closed – 0, open – 1.
- Parameter values should be time-related and vary with time; the time of telemetry sources should be synchronized. The frequency of data updates should range from 100 milliseconds to 24 hours.
- The values of the various parameters should be interconnected (by physical laws, control logic, process logic, etc.).
- The parameters should include those of most observational significance, and those that lie at (or as close as possible to) the root cause of the anomaly which is affecting various other parameters.
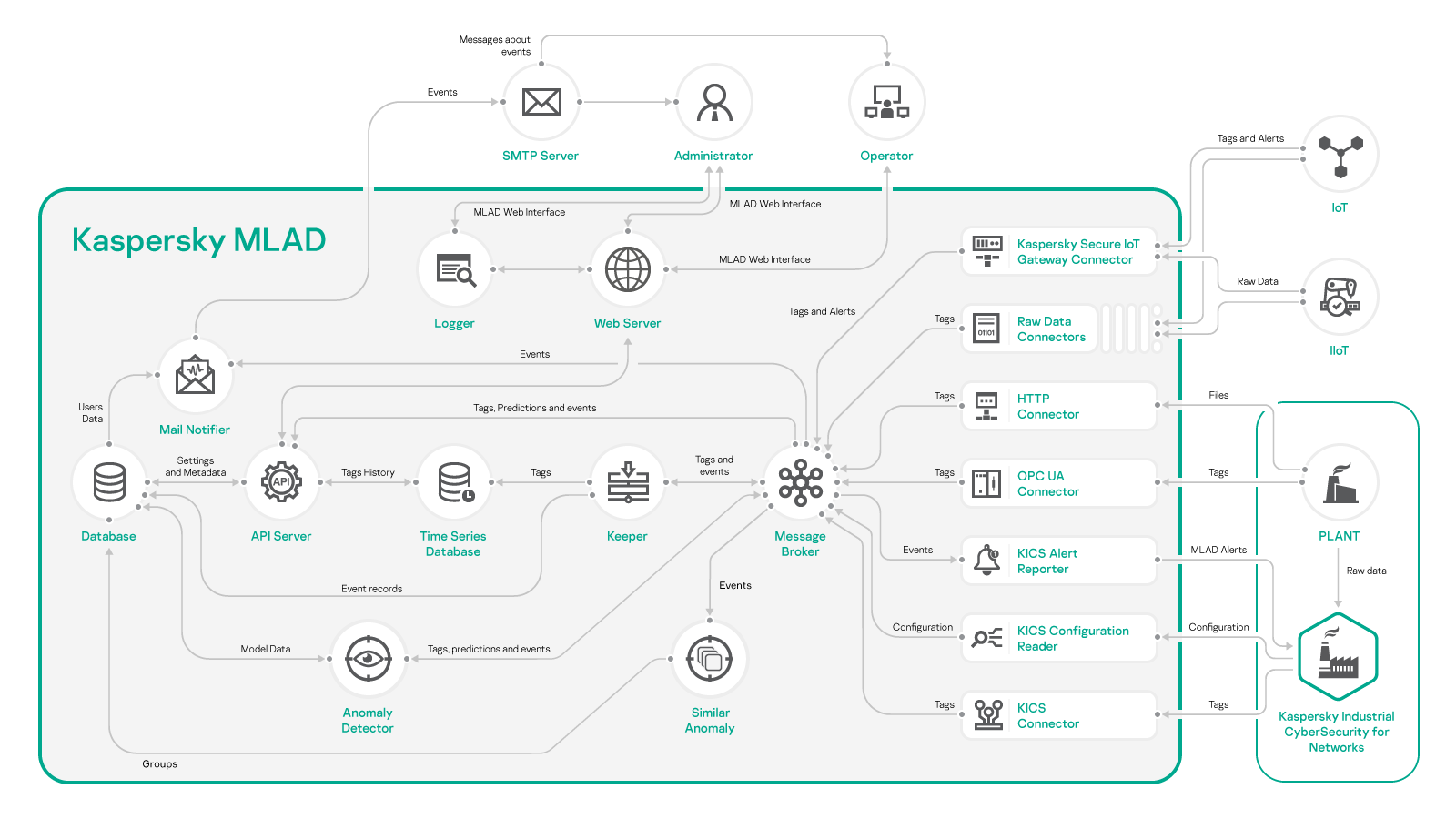
Kaspersky MLAD Engine
The engine is the set of basic system components supplied to each protected facility
Mandatory Kaspersky MLAD components
Anomaly Detector
Detects anomalies on the basis of data processing using the ML model
Similar Anomaly
Groups similar anomalies
Message Broker
Handles data exchange between Kaspersky MLAD components
Time Series Database
Stores received technological parameter values, ML model predictions, and prediction errors
Keeper
Routes messages for storage
Database
Used to store all Kaspersky MLAD settings
API Server
Ensures the operation of Kaspersky MLAD internal interfaces
Web Server
Ensures the operation of the Kaspersky MLAD web interface
Additional components
Logger
Stores Kaspersky MLAD functional logs
Mail Notifier
Sends alerts about anomalies
ML Model
The neural network model built by Kaspersky or a certified integrator for a specific protected facility. The ML model detects anomalies.
The ML model is not included in the product bundle, and is provided as part of Kaspersky MLAD’s model-building and integration services.
Connectors
The Kaspersky MLAD bundle includes services for data exchange with external systems. For each protected facility, one of the following connectors must be selected:
Set of connectors for interaction with Kaspersky Industrial CyberSecurity for Networks
KICS Connector
Receives process parameter values from Kaspersky Industrial CyberSecurity for Networks using the secure gRPC protocol
KICS Alert Reporter
Reports detected anomaly events to Kaspersky Industrial CyberSecurity for Networks using the secure gRPC protocol
KICS Configuration Reader
Receives configurations and technological parameter metadata from Kaspersky Industrial CyberSecurity for Networks using the secure gRPC protocol
OPC UA Connector
Receives data from an ICS using the protocol described in the OPC Unified Architecture specification
HTTP Connector
Receives data from an ICS by sending CSV files with tags through POST requests using the HTTP protocol