In the 1990s, engineers at Tennessee Eastman posted a detailed mathematical model of a chemical industrial process online. The primary reason was to refine various industrial process control models (PLC logic, etc.)
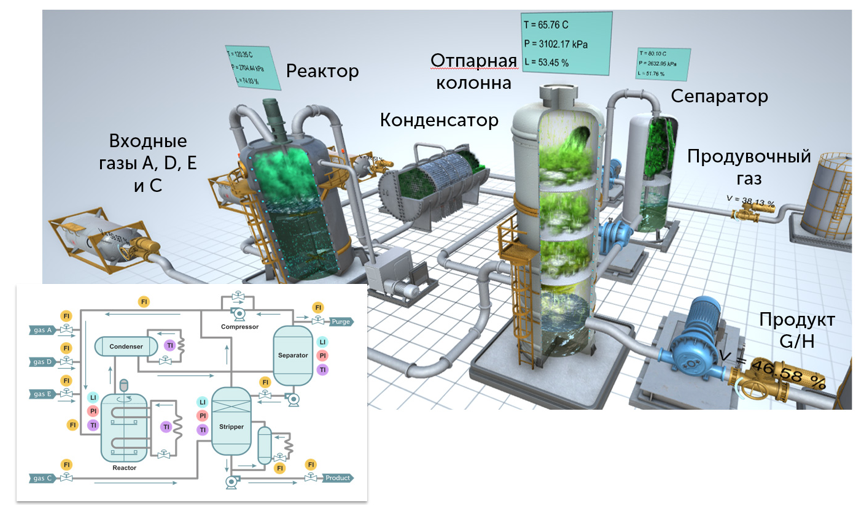
The Tennessee Eastman Process (TEP) model consists of four main units. Gases interact exothermically inside the reactor. The products leave the reactor as vapors and are fed into the condenser, then into the vapor-liquid separator. The liquid enters the stripping column, where the fractions are separated. The output consists of two products. This is a chemical manufacturing process. However, such units are typical of many industrial environments.
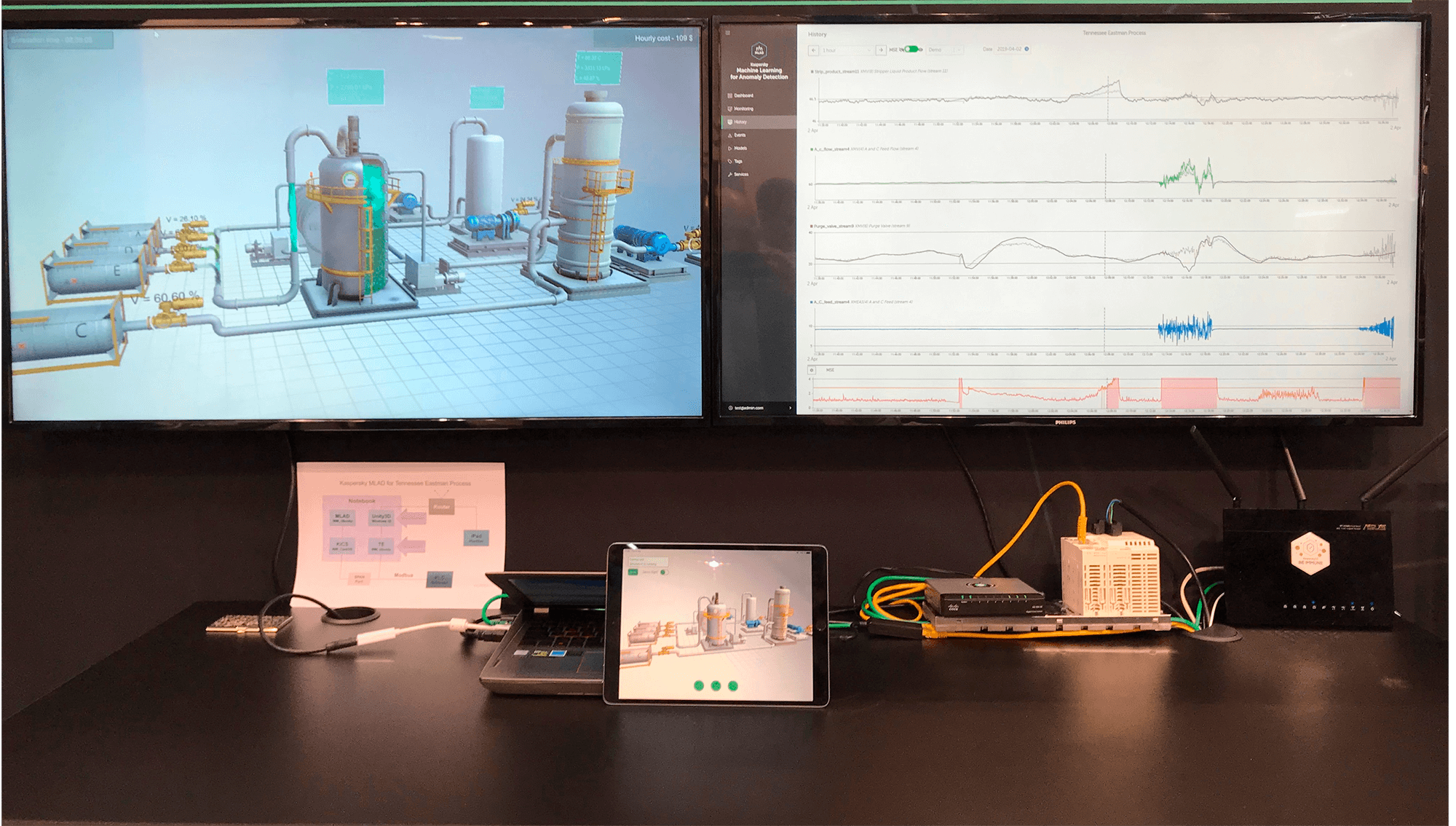
Based on the TEP model, we implemented a mathematical model in Python to simulate physical processes, as well as control logic for the physical model in the form of a PLC program. To visualize the simulated processes, we implemented a 3D TEP model and linked it with the generated physical model and PLC telemetry data. To control the stand, we developed a dedicated iPad console that can be used to simulate a variety of cyberattack scenarios. The result was a highly realistic chemical production simulator.
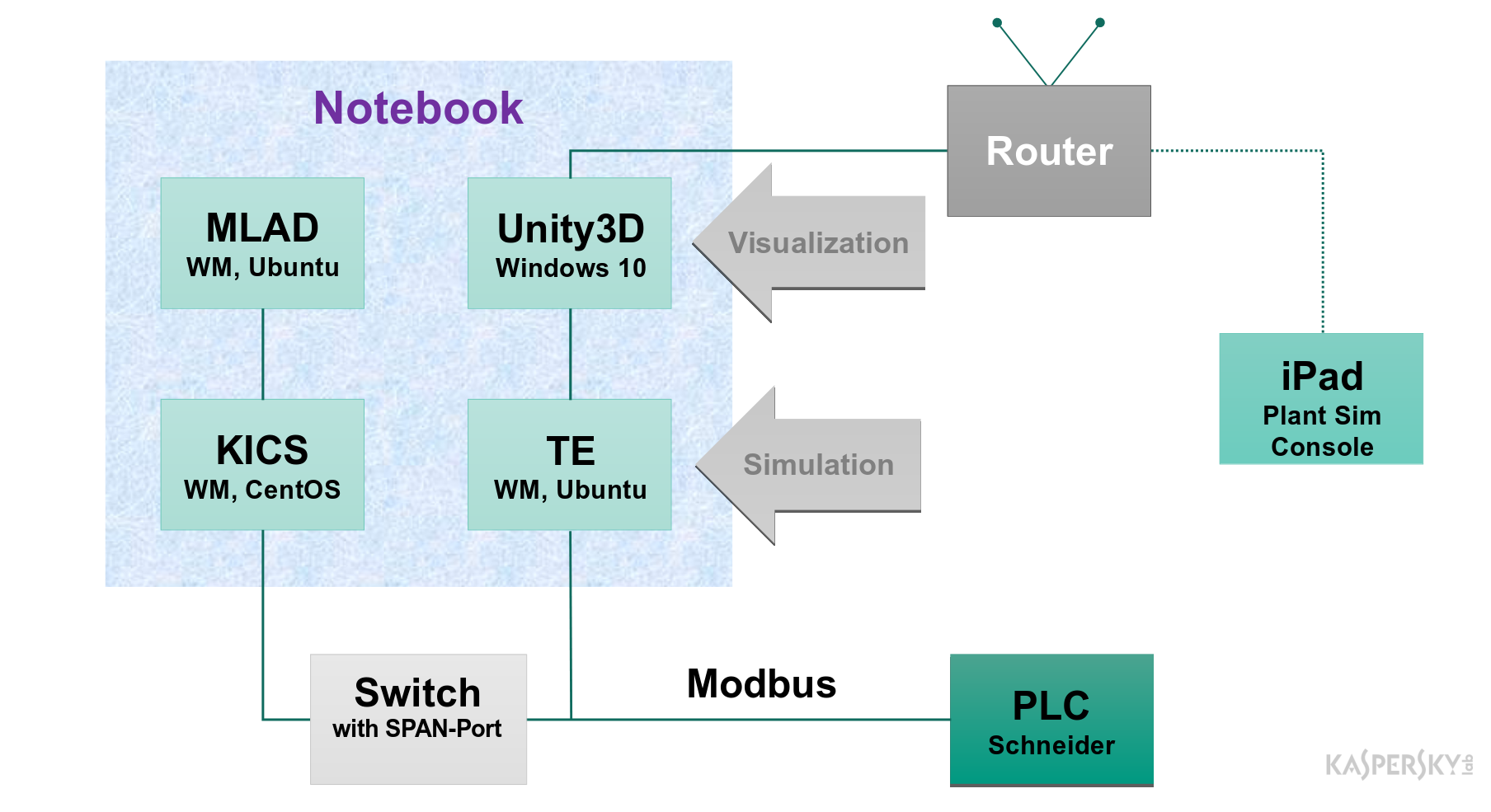
The TEP simulator is deployed on one laptop also running the mathematical model of the Tennessee Eastman Process and its 3D visualization. A Schneider controller is used as the PLC. Using a network switch, a copy of the process traffic of the chemical production simulator is sent to Kaspersky Industrial CyberSecurity for Networks, which parses the traffic and transmits the telemetry values obtained from it to Kaspersky MLAD.
Our TEP simulator has many parameters that we can control: both sensors and commands, totaling approximately 60 tags. Business parameters are also set, which allows us to calculate an enterprise’s operating costs (on an hourly basis). This helps to assess the overall damage from a hacker attack: an enterprise can suffer financial losses, even if an attack does not result in the worst possible outcome (an explosion or some other disaster).
Experimental attacks on the simulator show that Kaspersky MLAD detects anomalies in technological processes in their early stages, and is capable of covering a much wider range of connections between industrial signals than a traditional rule-based protection system can. In a traditional specialized protection system, rules are often generalized to match different conditions. This slows the triggering of emergency protection. A more finely tuned system based on machine learning responds earlier to anomalous changes in processes.
There are three gases. The sensors indicate how much gas is entering the reactor. According to the scenario, the attacker substitutes the value of a tag that corresponds to readings for gas supply sensor A, and the controller receives information that no gas is flowing. As a result, the controller opens the valve, increasing the gas flow. These incorrect sensor readings cause the controller to open the valve completely. The pressure in the reactor increases dangerously.
At the very start of the attack, Kaspersky MLAD detects an anomaly. In this instance, the pressure in the reactor reaches the threshold which triggers the emergency protection system (EPS) three hours after the attack starts (according to the internal simulation time). According to the scenario, the EPS has been turned off for some reason; had it been turned on, it would have been triggered a full three hours after the anomaly was detected by Kaspersky MLAD. In other words, from the moment that Kaspersky MLAD detects the anomaly until the attack enters its critical stage, the operator has enough time to take all necessary measures and prevent an accident. When MLAD detects an anomaly, the monitor displays detailed information about those signals where the error is most pronounced. This allows the operator to quickly locate the source of the problem and make the correct decision.